(Continued from the previous post)
The theory of regulated anonymity as propounded by Naavi advocates a conflict resolution solution for preserving the democratic principles of Privacy Protection in Cyber Space along with the need of the law enforcement to be able to prevent misuse of “Privacy” as a cover for Cyber Crimes.
The Theory is built on the premise that “Absolute Anonymity of the Netizen is impractical as it would be completely opposed by all law enforcement authorities and is against the current laws in most countries. Under the theory, Anonymity should be regulated by providing every Netizen with a “Cyber Space Avatar ID” to substitute the “Physical Space Citizen ID”. The Netizen may use his Netizen ID whenever he wants to be anonymous while he is free to do any transaction in Cyber Space also with the Citizen ID of the Physical Society. Whenever a justification arises for the Privacy wail to be lifted, a due process outside the control of the Government/Politicians/Corporate interests would be applied.
The assumptions under this theory are
a) Government of the day is not absolutely trusted by the Citizens and
b) Privacy law in most countries advocate a “Due Process” for lifting the privacy wail in the interest of national security etc. However the “Due Process” has a tendency to get corrupted in favour of an aggressive Government or influential corporate authority.
c) There is a need for an agency to act as an “Ombudsman” (Privacy Protection Group or PPG) between the Law enforcement authorities and the Citizen to decide when privacy wail can be lifted in the interest of national security and in accordance with the due process of law.
d) PPG has to be constituted outside the control of the major stake holders in privacy breach namely the Government, Politicians, and the Corporate powers.
e) Anonymity can be better preserved by distributing data across multiple persons and locations so that no single country or single person has all the data that are necessary for identifying a Netizen of the Cyber Society to a corresponding Citizen in the Physical world.
f) Necessary and Sufficient Penalties can be imposed on the Netizens applicable to Cyber Society independent of the penalties that can be imposed on the Citizen mapped to an offending the Netizen ID.
Suggested Process
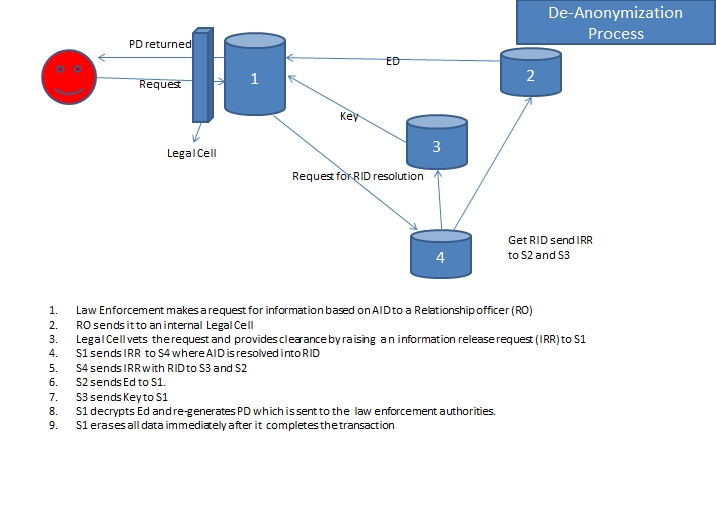
In pursuance of the above principles, the system of Regulated Anonymity recommended by Naavi is depicted in the following diagrams. The first diagram shows the suggested architecture for converting the Citizen ID to a Netizen ID and the second diagram shows how the request for the lifting of the privacy wail will function.
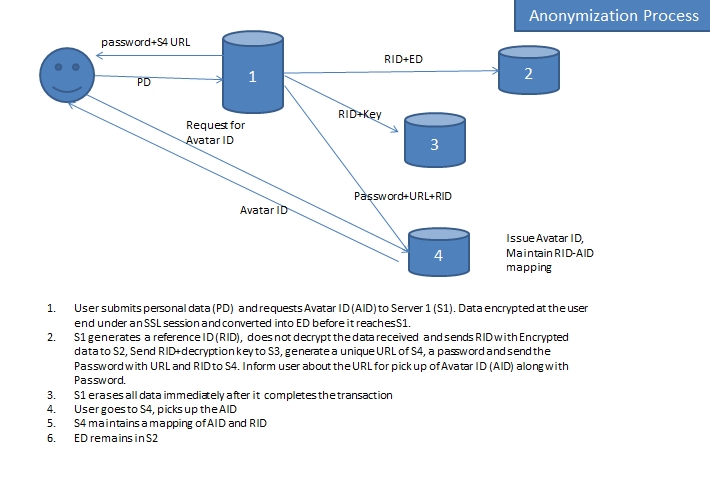
 In the above process, only for a brief period, private data will not be available in unencrypted form at any stage of anonymization. The decryption occurs only at the time of disclosure. These servers would be in different countries other than the country of residence of the user. The Netizen ID and its mapping to the ID required for accessing the data when required would be kept in a fourth server.
In the above process, only for a brief period, private data will not be available in unencrypted form at any stage of anonymization. The decryption occurs only at the time of disclosure. These servers would be in different countries other than the country of residence of the user. The Netizen ID and its mapping to the ID required for accessing the data when required would be kept in a fourth server.
This system ensures that data gets distributed over four different countries and servers and hence it would be difficult to forcefully access the data by any Governmental authority.
The process of revealing the personal data in case of a genuine need would be handled with a strong mechanism for filtering fake requests and unlawful requests. The body which filters the requests from law enforcement agencies will consist of experts in privacy law in different countries.
This process of Regulated Anonymity is expected to satisfy the Privacy requirements as well as the law enforcement needs.
It remains to be seen however who will venture into setting up the above system. It would be ideal that an organization like ICANN should take the lead in establishing such a system.
Naavi


