Section 66A of ITA 2008 has been one of the most abused sections of the Act in recent days. There is also a discussion about the constitutional validity of this section on whether this section infringes on the constitutional “Right to Freedom of Expression” as provided in Article 19(1) (a) of the Constitution. The discussion has arisen due to the filing of criminal cases in recent days in the case of Ravi Srinivasan of Pondicherry over a tweet, and two ladies in Palghar over postings in Facebook,
Article 19(1)(a) of the constitution is subject to “Reasonable Restrictions” as mentioned in Article 19(2) which provides discretion for any Government to frame and implement laws infringing on the freedom of expression under the following condition namely,
“in the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, public order, decency or morality or in relation to contempt of court, defamation or incitement to an offence”
The question therefore is whether Section 66A of ITA 2008 is a legislation framed under the exceptions provided under Article 19(2) of the Constitution.
This discussion would be relevant only if there is an impact of this section 66A on the “Freedom of Expression” under Article 19(1) in the first place. The perception of the community is of course that section 66A does infringe on the “Freedom of Expression” as otherwise the police action in the case of Ravi Srinivasan and the Palghar ladies were unwarranted.
However when we analyze the situation we need to also consider whether the action of the Police in the above two cases were in fact because the Police considered that Section 66A was an exception under Article 19(1) or simply because they misread the law.
If the Police had misread the law the remedy is not in removing the section but in punishing the Police for “Human Rights Violation” and providing such clarifications as would ensure that in future similar mistakes would not be done.
In this context it becomes necessary to discuss if Section 66A of ITA 2008 was indeed meant to address the situation where a Facebook post or a Twitter post could cause annoyance to another individual and that the person who had expressed the objectionable view could not be protected under Article 19(1).
Section 66A has three parts.
It is reproduced below for immediate reference.
Section 66A: Punishment for sending offensive messages through communication service, etc
Any person who sends, by means of a computer resource or a communication device,-
a) any information that is grossly offensive or has menacing character; or
b) any information which he knows to be false, but for the purpose of causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred, or ill will, persistently by making use of such computer resource or a communication device,
c) any electronic mail or electronic mail message for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages
shall be punishable with imprisonment for a term which may extend to three years and with fine.
Explanation: For the purposes of this section, terms “Electronic mail” and “Electronic Mail Message” means a message or information created or transmitted or received on a computer, computer system, computer resource or communication device including attachments in text, image, audio, video and any other electronic record, which may be transmitted with the message
This section applies to “Any Person” who “Sends” by means of a computer resource or a communication device, “any Information” or “Electronic Mail” or “Electronic Mail Message”.
It may be noted that this section is applicable to “Messages” and not for “Publishing” a content on a web platform. Under ITA 2008 offenses related to “Publishing” were covered under Sections 67, 67A and 67B and were restricted to content which was “Obscene”.
Then does it mean that ITA 2008 did not address situations where “Defamation” could occur through non obscene content being published on the web as in the case of the above cases?. The clear indication in the legislation is “Yes”. ITA 2008 did not try to address “Defamation” in electronic space except where the content was obscene.
The perception that Section 66A addressed defamation arose from the fact that it referred to “Information that is grossly offensive or menacing” under Section 66A(a) as well as “information” that could cause “annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred, or ill will” under Section 66A(b) and “Causing annoyance” under Section 66A(c).
The first time the section was invoked to address defamation was in the Delhi High Court case of E2labs Vs Zone-H.org. In this case the remedy sought was shutting down of a website which allegedly hosted some defamatory content. Since the defendant in this case was a foreigner and chose not to respond to the notices of the Court for reasons of his own, the Court passed an interim order blocking the website which has remained in place permanently since the defendant will never contest the injunction.
The interim judgement has therefore created a perception that the Court agrees that “Defamation” was caused by the publication and hence the site was blocked. This perception provides a sort of legitimacy to the claim that “Section 66A can be invoked when defamatory content is published on the web platform and it does not get restricted by the constitutional rights of freedom of expression”.
It must however be noted that Section 66A was meant to address “Information” that can be “Sent” and not “Information which is static”. Information which is “Sent” is a “message” and is sent from one person to another. It is “Pushed” . On the other hand a content which is “Posted” is not directed at any person. It is only “Pulled” by persons who have become part of a “Community” who have agreed to exchange information with other members of the community.
A “Facebook” post or a “Twitter Post” falls into this category of “Hosted content” and does not fall into the category of “messages”. They can be dealt with under the Section 499 of IPC and there is no need to invoke Section 66A.
The fact that Section 66A was meant for “messages” is also evident from the fact that Section 66A(b) used he word “Persistently”. This means that if a person is again and again sending a message (which he knows to be false and is sending it with the malicious intention of causing annoyance etc). In a website posting, the content is posted and not sent again and again to another person.
Section 66A(a) does not use the word “Persistently” but it applies only to such messages which can be considered as “Grossly offensive or Menacing”.
Section 66A(c) also does not use the word “Persistently” but it is specifically mentioned that it is addressed to an “Electronic Mail”.
Thus it can be inferred that Section 66A was meant only for “messages” and not for “Content”. This is justifiable since Section 499 may not be apt for “letters sent from one person to another” and also that the web presented the possibility of a higher level of annoyance than the physical equivalent of “Bulk letter mailing” since “Bulk email bombardment” is more likely.
Section 66A addressed the message because there were offences such as Cyber bullying and Cyber Stalking as well as “Spam” which could not be effectively dealt with under Section 499.
In view of the above we can conclude that Section 66A ITA 2008 was never meant to address “Defamation” and never meant to overlap Section 499 of IPC but was meant to address situations which in the cyber space were significant threats and were not addressed effectively by the physical world equivalent addressed by IPC.
If therefore we come to the conclusion that “No change is required in Section 66A” it will be because the section was never meant to address “Defamation” and exclusions under Article 19(2) of the constitution and not because we endorse the view that Section 66 A is within the constitutional validity of Article 19(2).
Media needs to understand the issues involved and does not misinterpret the views that may be expressed by the Court in this regard.
Naavi



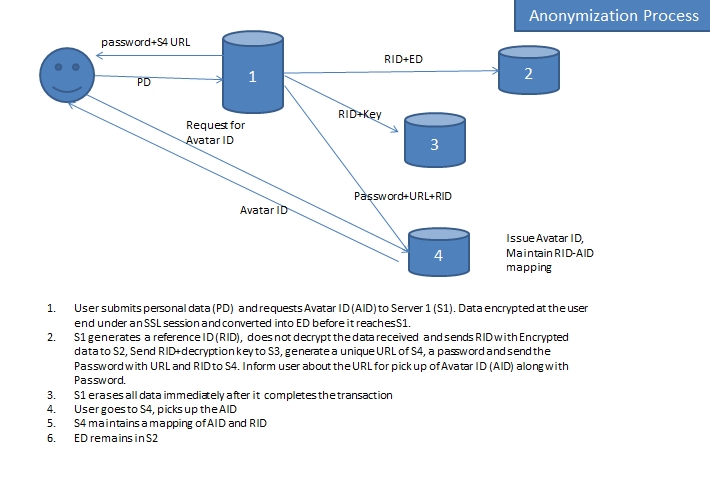
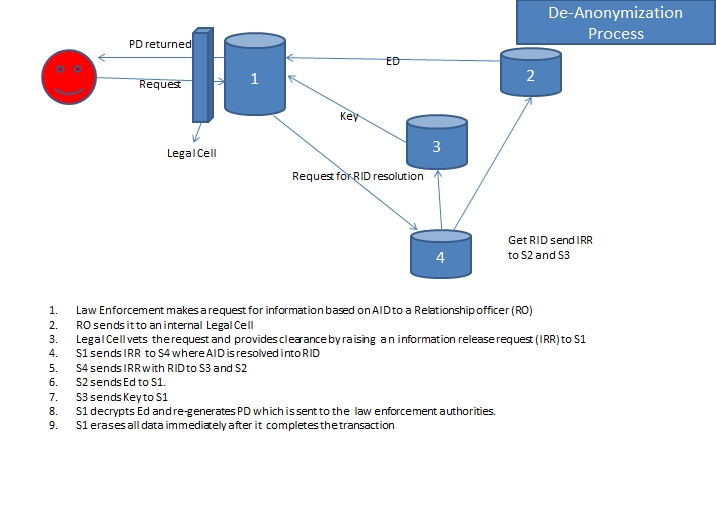 In the above process, only for a brief period, private data will not be available in unencrypted form at any stage of anonymization. The decryption occurs only at the time of disclosure. These servers would be in different countries other than the country of residence of the user. The Netizen ID and its mapping to the ID required for accessing the data when required would be kept in a fourth server.
In the above process, only for a brief period, private data will not be available in unencrypted form at any stage of anonymization. The decryption occurs only at the time of disclosure. These servers would be in different countries other than the country of residence of the user. The Netizen ID and its mapping to the ID required for accessing the data when required would be kept in a fourth server.